Critical JavaScript Vulnerability Warns of On-Chain Transactions
The cryptocurrency world is still reeling from a shocking cybersecurity event that occurred on September 8, 2025 — a massive supply chain attack on Node Package Manager (NPM), the backbone of JavaScript development.
9/9/20253 min read

The breach hit directly on-chain
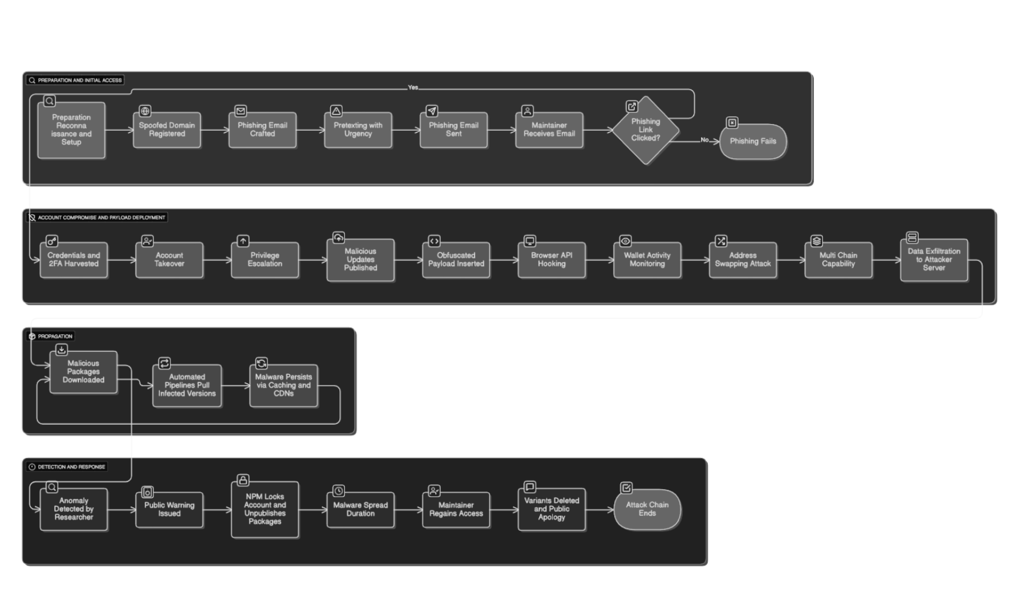
The story begins with a phishing email posing as official NPM support, sent from a fake domain (npmjs.help) to maintainer Josh Junon, known online as "Qix-."
The message, timestamped at around 13:00 UTC on September 8, warns of an impending account lockout on September 10 unless two-factor authentication (2FA) is “updated” via the malicious link.
“As part of our ongoing commitment to account security, we require all users to update their two-factor authentication (2FA) information,” the post reads, mimicking legitimate NPM wording to create confusion.
Junon, an active contributor whose packages are co-maintained with lead maintainer Sindre Sorhus, was active for a "stressful week," giving the attacker complete control.
In just a few minutes, hackers pushed malicious updates to 18 core extensions, inserting hidden malicious code that was able to evade basic scans.
Malware researcher Charlie Eriksen of Aikido Security discovered the anomaly at 13:16 UTC—just five minutes after publication—and made the report public within an hour.
This code connects to browser APIs (e.g. fetch, XMLHttpRequest, window.ethereum) to monitor wallet activity, then swaps the recipient address with an attacker-controlled address that looks similar.
Users see the desired address on the screen but sign a fake transaction, a tactic reminiscent of the $1.5 billion theft of Bybit by North Korea's Lazarus Group in early 2025.
Unconfirmed reports suggest the possibility of seed pods being harvested, though Guillemet notes on X that the issue is still under investigation.
The malware targets multiple chains—Bitcoin (bech32), Ethereum (0x), Solana (base58), Tron, Litecoin, and Bitcoin Cash—by stealing data on websocket-api2.publicvm.com.
Build-time errors in older Node.js environments (unsupported fetch) ironically aided detection, as the payload silently failed in some tests.
Is the ecosystem collapsing?
The JavaScript and cryptocurrency communities were quick to rally. Guillemet's warning — shared more than 15,000 times on X — emphasized hardware wallet verification: "Pay attention to every transaction before signing and you will be safe." Software users were asked to "not make any transactions on-chain at this time."
Solana's ecosystem, which relies heavily on JS, has made blanket commitments: Jupiter confirms no SDK/UI vulnerabilities; Drift has paused pre-transactions; Marinade Finance reports a clean codebase but urges caution.
Aptos Petra wallet has paused its release for testing, while ChainArq and TokenOS claim there is no dependency on the tainted packages.
Larger DeFi entities like Aave and Uniswap have monitored user interfaces, but no vulnerabilities have been confirmed as of September 9.
This follows the 2025 "s1ngularity" Nx attack (August), in which AI tools stole GitHub secrets from 2,180 accounts, and the eslint-config-prettier breach in July (30 million downloads).
Scams are still rampant, with Chainalysis recording 32% of cryptocurrency losses coming from these types of scams.
Threats to blockchain
GitHub (owner of NPM) has pushed to requiring mandatory 2-factor authentication (2FA) for maintainers until the end of the year, while tools like Socket's AI scanner (which flagged this) are gaining traction.
Bug bounties through Immunefi have prevented $25 billion in losses, but trust in open source is eroding—developers now favor SRI (Sub-Resource Integrity) and code signatures.
It is estimated that cached malware may exist in 10-20% of unpatched applications, posing a potential loss of over $500 million if not mitigated.
Steps to fix:
User: Hardware (Ledger/Trezor): Clear all transactions. Software (MetaMask): Pause; check recent transactions in browser.
Developers: Run npm ls for deps; override in package.json (eg: {"chalk": "^5.3.0"}); rebuild; follow npm notices.
Wallet: Verify address manually—don't trust the UI.
Disclaimer: The information presented in this article is the author's personal opinion on the cryptocurrency field. It is not intended to be financial or investment advice. Any investment decision should be based on careful consideration of your personal portfolio and risk tolerance. The views expressed in the article do not represent the official position of the platform. We recommend that readers conduct their own research and consult with a professional before making any investment decisions.
Explore HCCVenture group
HCCVenture © 2023. All rights reserved.

Connect with us
Popular content
Contact to us
E-mail : sp_contact@hccventure.com
Register : https://linktr.ee/holdcoincventure
Disclaimer: The information on this website is for informational purposes only and should not be considered investment advice. We are not responsible for any risks or losses arising from investment decisions based on the content here.

TERMS AND CONDITIONS • CUSTOMER PROTECTION POLICY
ANALYTICAL AND NEWS CONTENT IS COMPILED AND PROVIDED BY EXPERTS IN THE FIELD OF DIGITAL FINANCE AND BLOCKCHAIN BELONGING TO HCCVENTURE ORGANIZATION, INCLUDING OWNERSHIP OF THE CONTENT.
RESPONSIBLE FOR MANAGING ALL CONTENT AND ANALYSIS: HCCVENTURE FOUNDER - TRUONG MINH HUY
Read warnings about scams and phishing emails — REPORT A PROBLEM WITH OUR SITE.
